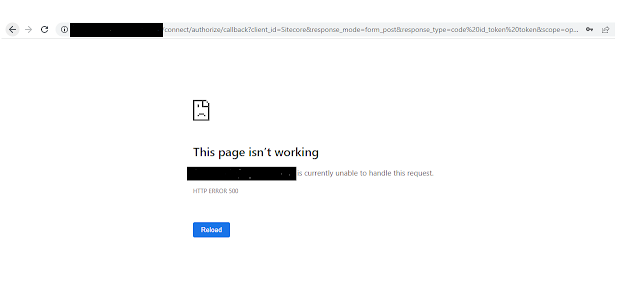
Sitecore Error: Unhandled exception: "Keyset does not exist"
A few days back, I changed the certificate on the Content Management server, after that, I was not able to login into the Content Management Server. It was throwing the below error:
Solution:
After some investigation I found that my new certificate which I was using for the Identity server, does not have the permission of the Identity App Pool so I followed the below steps:
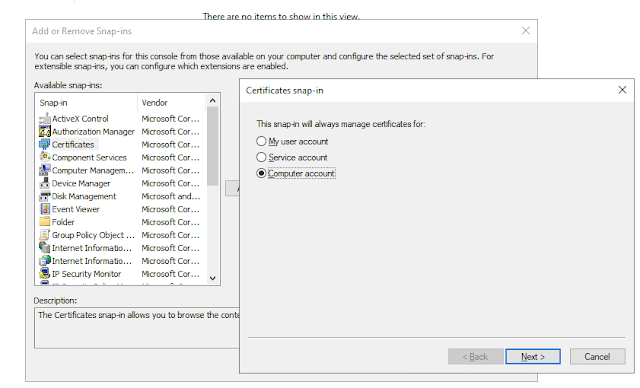
- Enter "mmc" in the run command window.
- Click on Add/Remove Snap-ins option inside the File menu.
- Select Certificates and click on Add button, then select Computer account and click on Next->Finish->Ok
- Go to the Personal-> Certificates.

- Now right-click on the Identity server certificate, then click All Tasks-> Manage Private Keys.
- Click on Add button and add IIS App Pool\Identity.XXX permission.
- Click on Check Name, and give read access.
I hope it will work for you. Happy coding :)

Comments